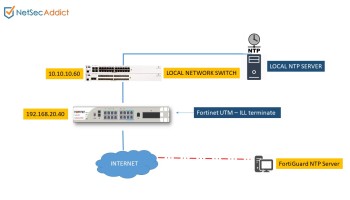
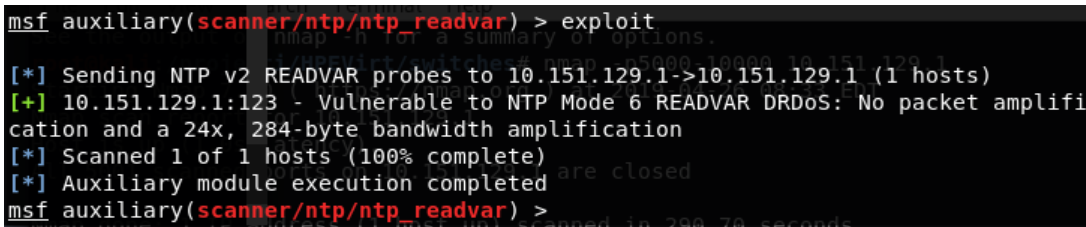
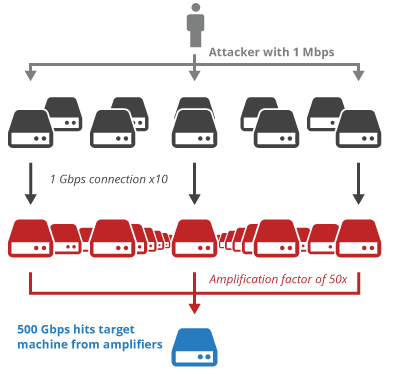
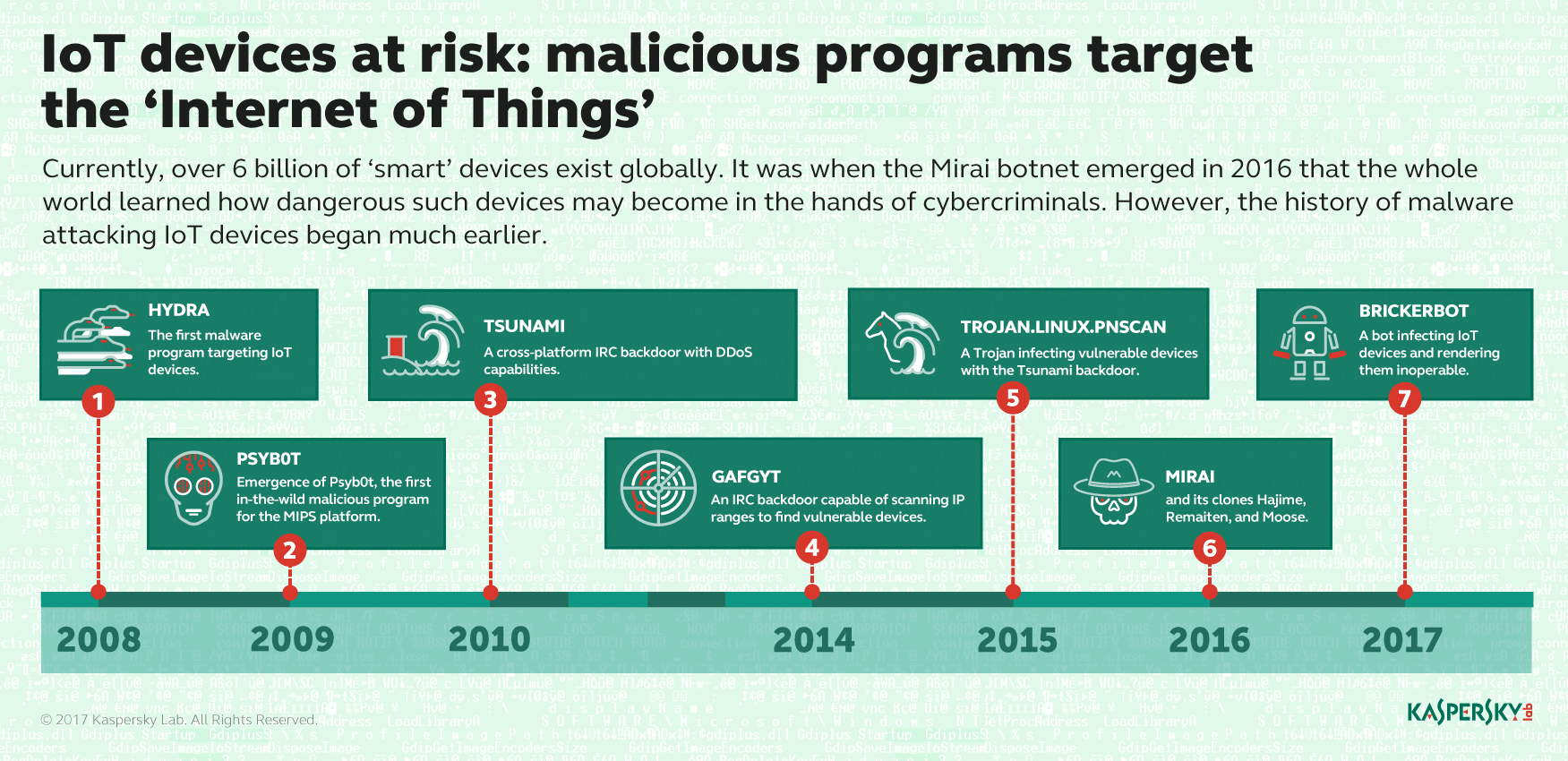
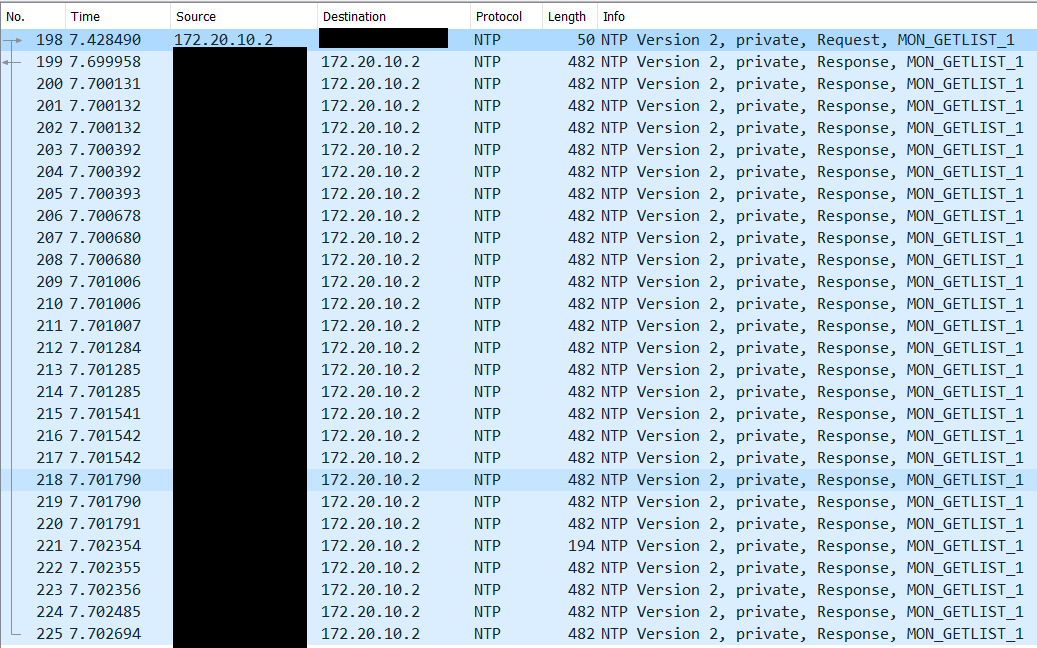
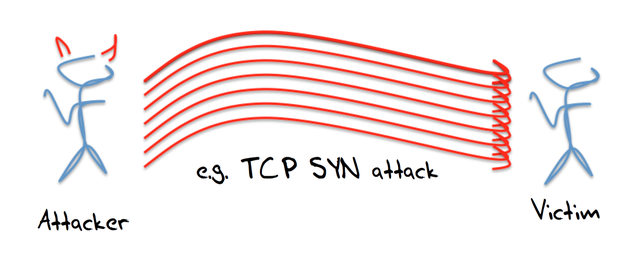
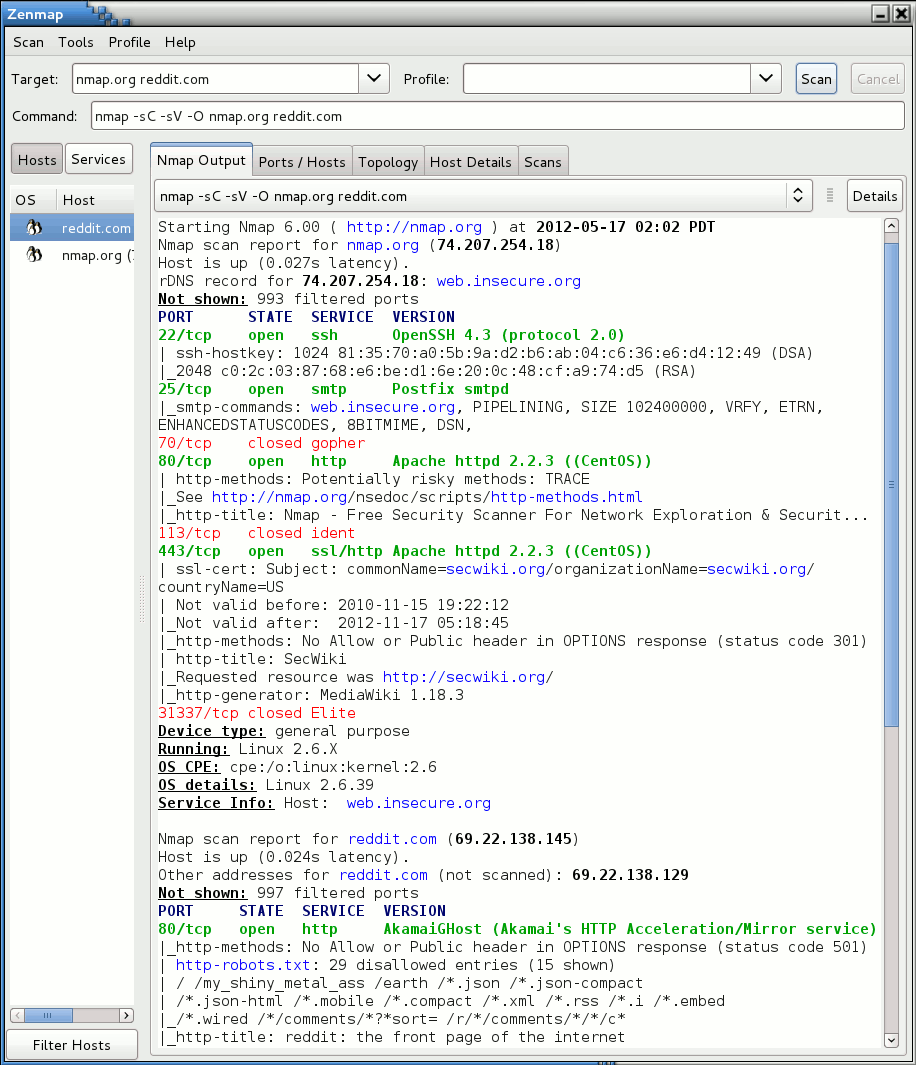
How to configure Network Time Protocol (NTP) Mode 6 Scanner in Cisco Switches? | Network and Security Solutions

How to configure Network Time Protocol (NTP) Mode 6 Scanner in Cisco Switches? | Network and Security Solutions

How to configure Network Time Protocol (NTP) Mode 6 Scanner in Cisco Switches? | Network and Security Solutions